In 59 Categories,
Spanning The Top 348,565 Projects
Social Media 📦 27
Web Servers 📦 26
Mathematics 📦 55
Text Editors 📦 49
Blockchain 📦 73
Software Development 📦 72
Bibliothèques, architectures d'indexation, Babel moderne, rayons de connaissances.
Trier, un art, une science, un commun spécialisé.
Tour d'horizons de ces pratiques autour de séminaires-rencontres.
Google Captchas
Spying and detect false humains
How to ? It's secret for good...
Remembering onions 2017 ( avec @Roger_Dingledine (où?, ajouter.ref) )
" Over the years the Tor community has come up with various ways of handling these large and non-human-memorable onion addresses. Some people memorize them entirely or scribe them into secret notebooks, others use tattoos, third-party centralized directories or just google them everytime. We've heard of people using decks of cards to remember their favorite onion sites, and others who memorize them using the position of stars and the moon. "
How the Net Works
Standards for identifying devices on the network
Domain names and IP addresses
Protocols for sending information through the network
Following your information on the Internet - the journey
Network Toplogies
Link Density
...
Paul Baran’s three topologies of networks: centralized, decentralized, distributed.
traceroute
Simplified model of the internet. It’s made of routers. Home devices are connected to your router, which is connected to your internet network provider. Business and academic networks are similarly made up of individual computers connected to local routers, which are, in turn, connected to those institutions’ network providers. Mobile devices are connected to mobile network providers, and those providers in turn connect to other network providers to make sure your texts get to your friends phones and computers.
What is BGP?
BGP is the protocol that makes the Internet work. ///Border Gateway Protocol (BGP) submits data across the internet and is responsible for selecting the best route from all the available paths that data can travel, which usually means hopping between autonomous systems.
BGP is not perfect
The Protocol on which the Internet is built is outdated
BGP is now 20+ years old.
Derière ce projet, Syntropynet
"Syntropy is an open project providing next-generation connectivity technology for the Internet."
En français cours internet :
https://youtu.be/uzRgR39uMz0?t=193
NOIA NETWORK
. un BGP par blockchaine !
. Répondre à l'hyper communication actuelle...
Token vendu sur Coinbase...
. Space-sharing, partage de HDD (P2P, localiste, data-center partout)
Vérifier tout un ensemble de failles-vulnérabilités-singularités de votre Navigateur préféré ! //WebRTC leak, //Fingerprint, //adresse IP...
A COLLECTION OF ORIGINAL PHONES FROM THE TECHNOLOGICAL INTERBREEDING MADE IN CHINA 2017
ONGOING RESEARCH: Shanzhai Archeology casts a critical look at the production of technology through an artistic interpretation of a recent historical fact, still poorly known: the shanzhai. Often presented as mere counterfeits of low quality, these objects nevertheless draw many unusual technological trajectories that make them the revealers of technological possibilities literally out of European standards. As odd looking hybrids, these puzzling artefacts question a hyper-normalised western technological imaginary.
Conception: Nicolas_Maigret , Clément Renaud & Maria Roszkowska (DISNOVATION.ORG)
The Lumen Database, a project designed to facilitate research on takedown notices, has made a significant change to the way it offers data. While it will still be possible for researchers to access data with a special login, regular users will have to apply via email to see the details of a notice in full. The changes have been made in preparation for an expansion of its operations.
...
“Lumen wants to remain a vibrant and valuable feature of the landscape with respect to research, journalism, and public awareness around takedown requests. We believe that we have been successful at doing this over the years and that some great work has come out of, or been predicated on, our data,” Holland says.
Academic Search Engine
alt.Google_Scholar
J'aime beaucoup ce que nous raconte les artistes dans cette vidéo
Elle révelle surtout la géométrie variable avec laquelle les "Darknets" sont traité... ou plutôt le principe de l' obfu_secret fondamental aux banques et super-marchés connectés.
De tous ces espaces fermés, heureusement secrtes-privés...
ces réseaux réservés qui appartienet au DeepWeb parcequ'effectivement on ne peut les indexer, en tirer des données (au moins de la part de la concurence et certains bot_scraper ( on omet un peu vite les traitements de données internes aux entreprises qui voudraient faire fructifier les données dormantes ou darkdatas... ). Mais oui, en effet le bot de Gogle ne va pas où il veut et c'est bien comme ça.
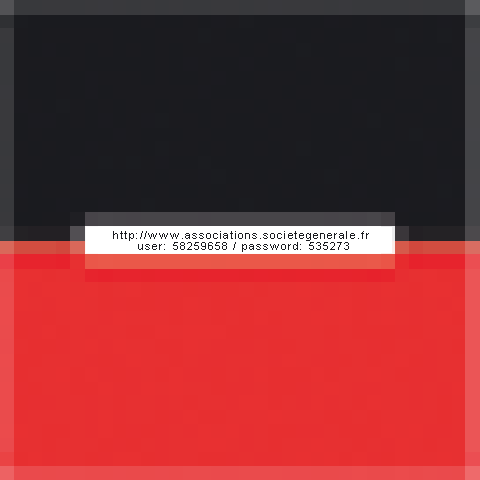
Bon bin des fois l'errreurrr est humaine et les portes s'ouvrent...

Que se passe t il quand on laisse les clefs de son compte banquaire à Internet ?
Quand on fait de cet espace symboliquement le plus privé et sécurisé, un espace de intrusion_vulnérabilité volontaire ? Un espace_public dans le cyber_espace ? C'est ce que nous racontent ces deux artistes.
@Ferenc_Gróf and @Jean-Baptiste_Naudy
installation pour les RIAM 06 à Marseille en 2009
http://www.riam.info/06/indexb379.html
alt.vidéo : https://www.youtube.com/watch?v=qF1qPgM-WUo
( leur site est .dead http://www.societerealiste.net )
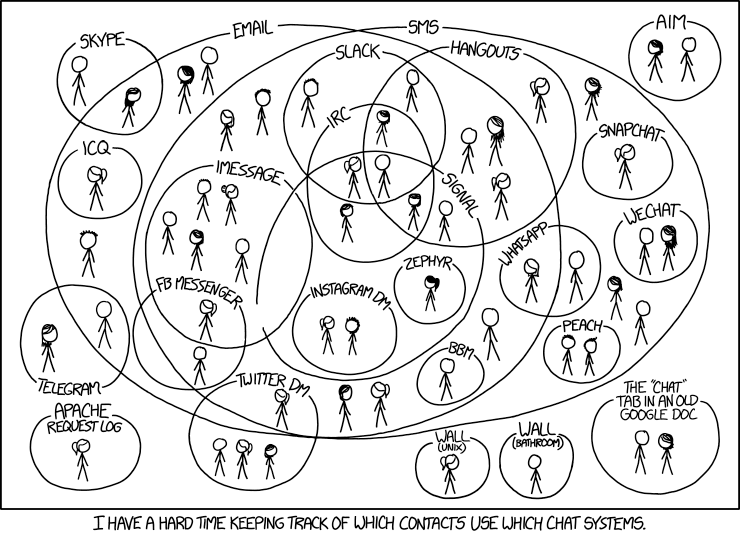
Nos amiEs répartiEs selon leur chat
quelle distance entre nous ?
quelle exclusion de nos sphères sociales ?
quelle perte-division d'attention ?
quelle décentralité ?
quelle interopérabilité ?
quelle hermétique à ces réseaux_bulles ?
...
Isolation de bulles numériques
multi-canaux
attention divisée
"Can you hear me?"
Hello NSA , hello GCHQ. Berlin speaking here.
¥ Antennas on the Academy of Arts in Berlin
Messages can be sent to the intelligence agencies on the frequencies that are intercepted by the NSA and GCHQ. An independent mesh network in Berlin's Government District recaptured the virtual communication space. A collective conversation space in which all have equal rights has been taking the space of secret wiretapping.
http://www.statemachines.eu/projects/708/
http://www.statemachines.eu/projects/708/ =
AN ARCHEOLOGY OF SILENCE IN THE DIGITAL AGE
“I have not tried to write the history of that language (A/N the language of psychiatry) but, rather, the archeology of that silence.”
M. Foucault, Madness and Civilization, 1961
Artists @Christoph_Wachter and @Mathias_Jud have been paying special attention to the different forms of silence that prevail on the Internet. With their work, they aim to undermine power structures while also developing tools and systems of communication for those in need. They uncover network mechanisms, expose cases of censorship and surveillance, and embrace infrastructural literacy as a response to the dominance of today’s network ( 2017 )
Via https://www.wachter-jud.net/Can-you-hear-me.html?r9t_locale=en
Au programme de @State_Machines ( thématique_revue ) ...
0n retrouve : @The_Critical_Engineering_Working_Group et @Aksioma #<3
Voici une liste des articles de presse concernant la campagne /TellTheTruthBelgium/. Voilà un bon début avec le lancement du faux discours de la première ministre Wilmès.
XR victime à son tour de contrefaçon :
https://fullfact.org/online/Extinction-Rebellion-Sticker/
- Museum of fake Websites
https://theyesmen.org/fake-websites
"These are some of the websites in the course of Yes Lab and Yes Men projects, since 1999 , in reverse chronological order."
- En outre des sites parodiques militant les Yes Men se font connaitre par leur activités comiques mais politiques ( 2001 ~ 2004 + )
Ils usurpent l'identité numérique de sites respectables (au design vernis) comme cheval de trois des organisations méta gouvernementales tel l'OMC. Ils usent d'une légitimité d'apparence.
···
Cette attaque qualifiable de "pot de miel" ( honeypot ) leur donne accès à l'espace attentionel d'organisations ciblées. Ils abusent en fait du billai cognitif faisant qu'on attribut plus facilement du crédit aux représentants de pouvoir (portant une blouse, professeurs, etc), nous nous laissons prendre par leur aura brillante (Effet Barnum).
...
Leur but final est d'exposer des partisans-alliés de la doctrine libérale à sa caricature. Ils tendent par la même occasion ( le temps limité de leur infiltration ) à éprouver l'élasticité éthique des entreprises : jusqu'où ces organisations sont prêtes à aller pour le profit.
Les Yes Men sont à l'origine de fausses nouvelles, rumeurs (dont la parution d'un journal de nouvelles utopistes reprenant le design du New York Times).
Ils profitent d'une usurpation d'identité de l'entreprise DOW**** pour annoncer sur un plateau télé américain la reconnaissance de cette entreprise pour les dégâts sanitaires, humains et écologiques durant un grave accident. Ils réactivent ainsi cette mémoire et le devoir de réparation : ils re-politisent et réactivent le fait historique trop vite oublié.
The Anti-Advertising Agency was a collaboration between myself and dozens of other artists working on the themes of advertising and public space. I planned on running the project for one year and in that time the AAA project exceeded my expectations in every way. Over the last six years I’ve worked with some amazing people, made things we never thought possible, and even removed a few billboards.
par Ben_Grosser 2015
computational surveillance system
Tracing You presents a website's best attempt to see the world from its visitors' viewpoints. By cross referencing visitor IP addresses with available online data sources, the system traces each visitor back through the network to its possible origin. The end of that trace is the closest available image that potentially shows the visitor's physical environment. Sometimes what this image shows is eerily accurate; other times it is wildly dislocated. What can a computational system know of our environment based on the traces we leave behind? Why might it want to see where we are?