Quelles sont les options ?
Trouver un hébergement et un nom de domaine
Suggestions pour trouver hébergement et domaines
Utiliser un outil en ligne comme GitHub
Utiliser un EDI web tel que Thimble*
Publier via GitHub
Lectures pour approfondir dont
https://www.codecademy.com/learn/deploy-a-website
- migré vers http://glitch.me/
JSFiddle
JSBin
CodePen
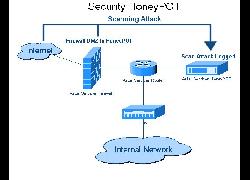
"Dans le jargon de la sécurité informatique, un honeypot est une méthode de défense active qui consiste à attirer, sur des ressources, des adversaires déclarés ou potentiels afin de les identifier et éventuellement de les neutraliser."
Projet de lutte contre le spam
https://www.projecthoneypot.org/
HP en français, leur fonctionnement, les stratégies, quelques tutos ressources
http://igm.univ-mlv.fr/~dr/XPOSE2009/botnets/honeypot.html
Liste d'HP en anglais
https://github.com/paralax/awesome-honeypots
https://www.smokescreen.io/practical-honeypots-a-list-of-open-source-deception-tools-that-detect-threats-for-free/
A project by @Joana_Moll
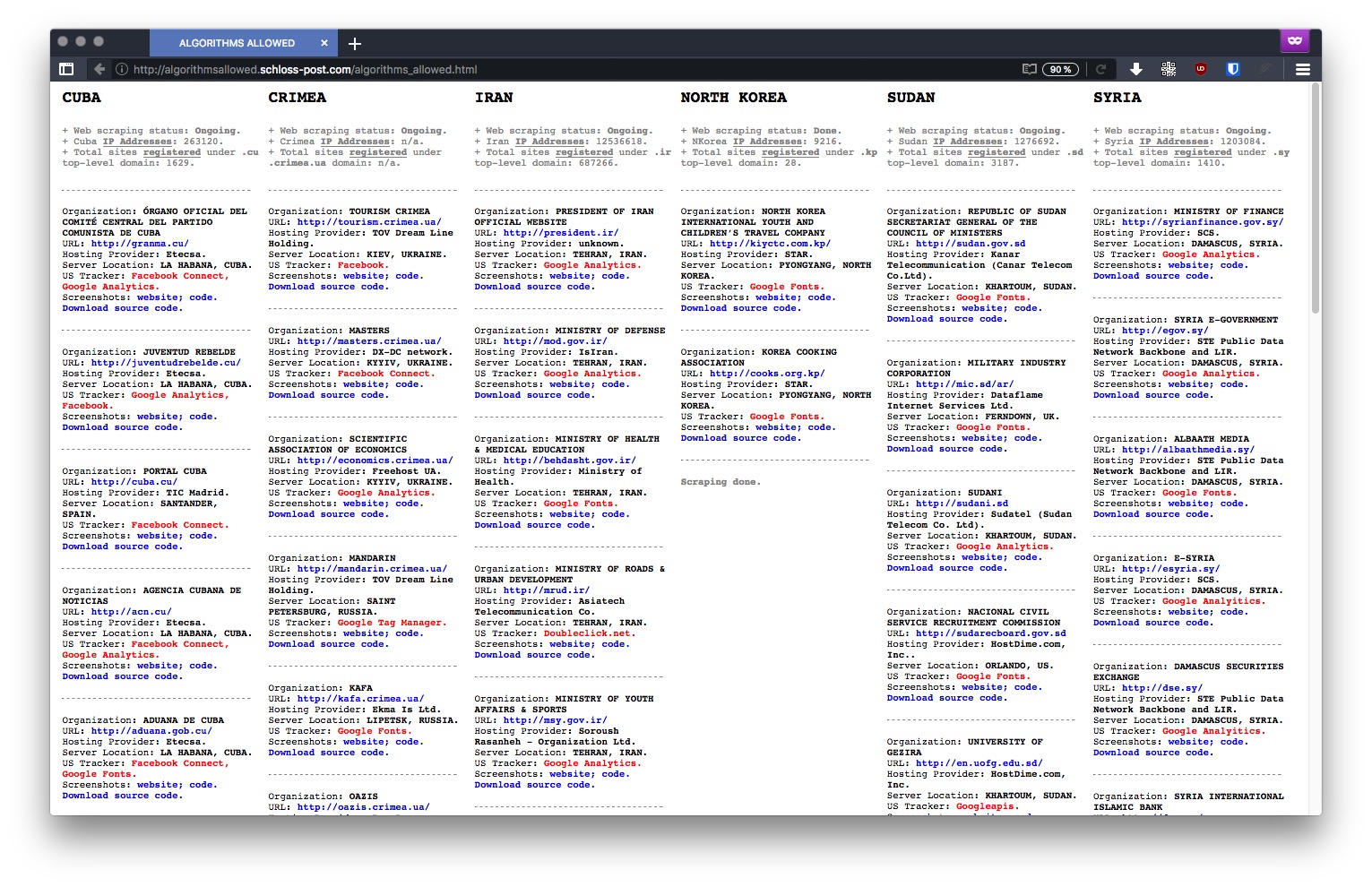
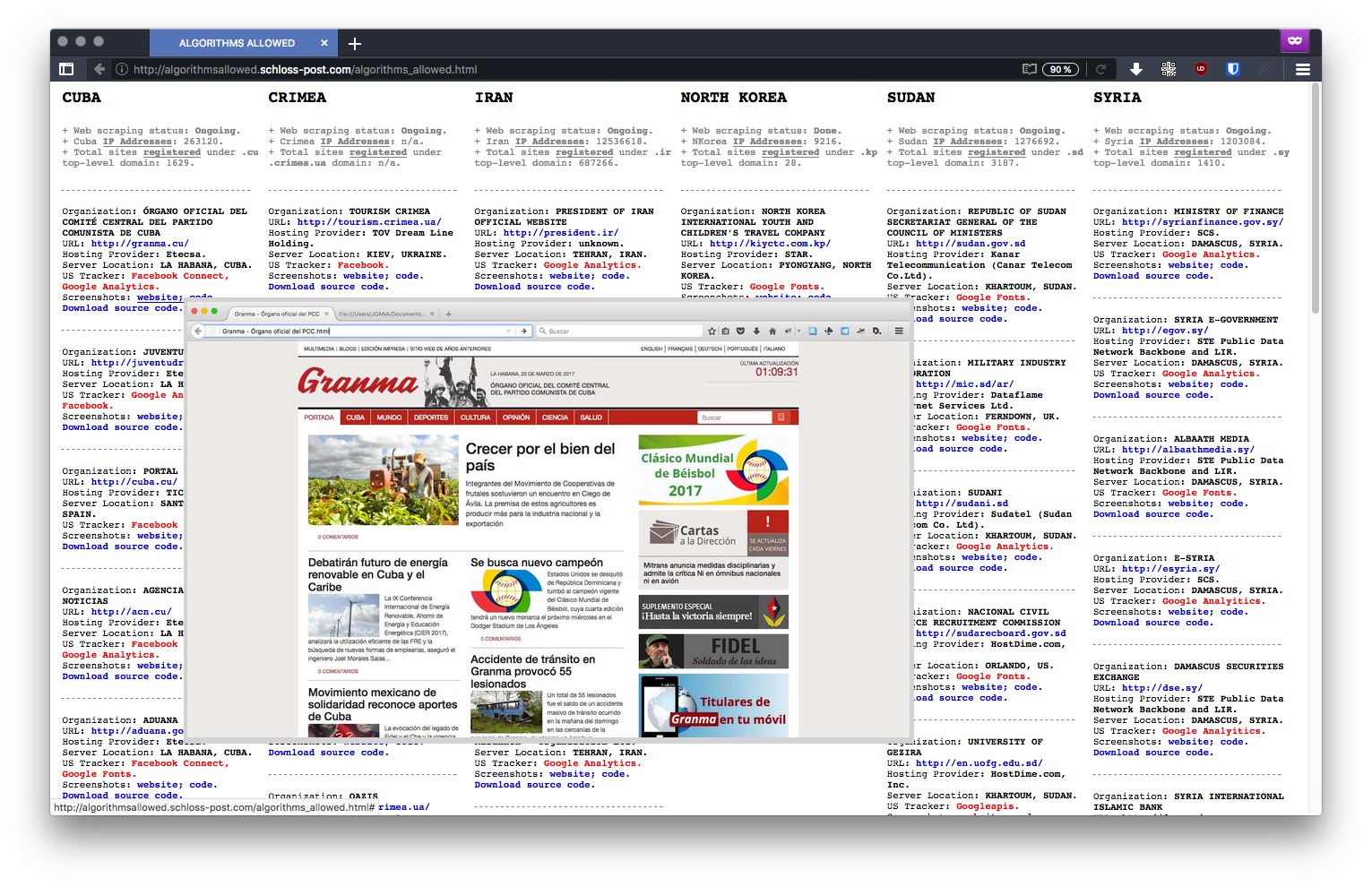
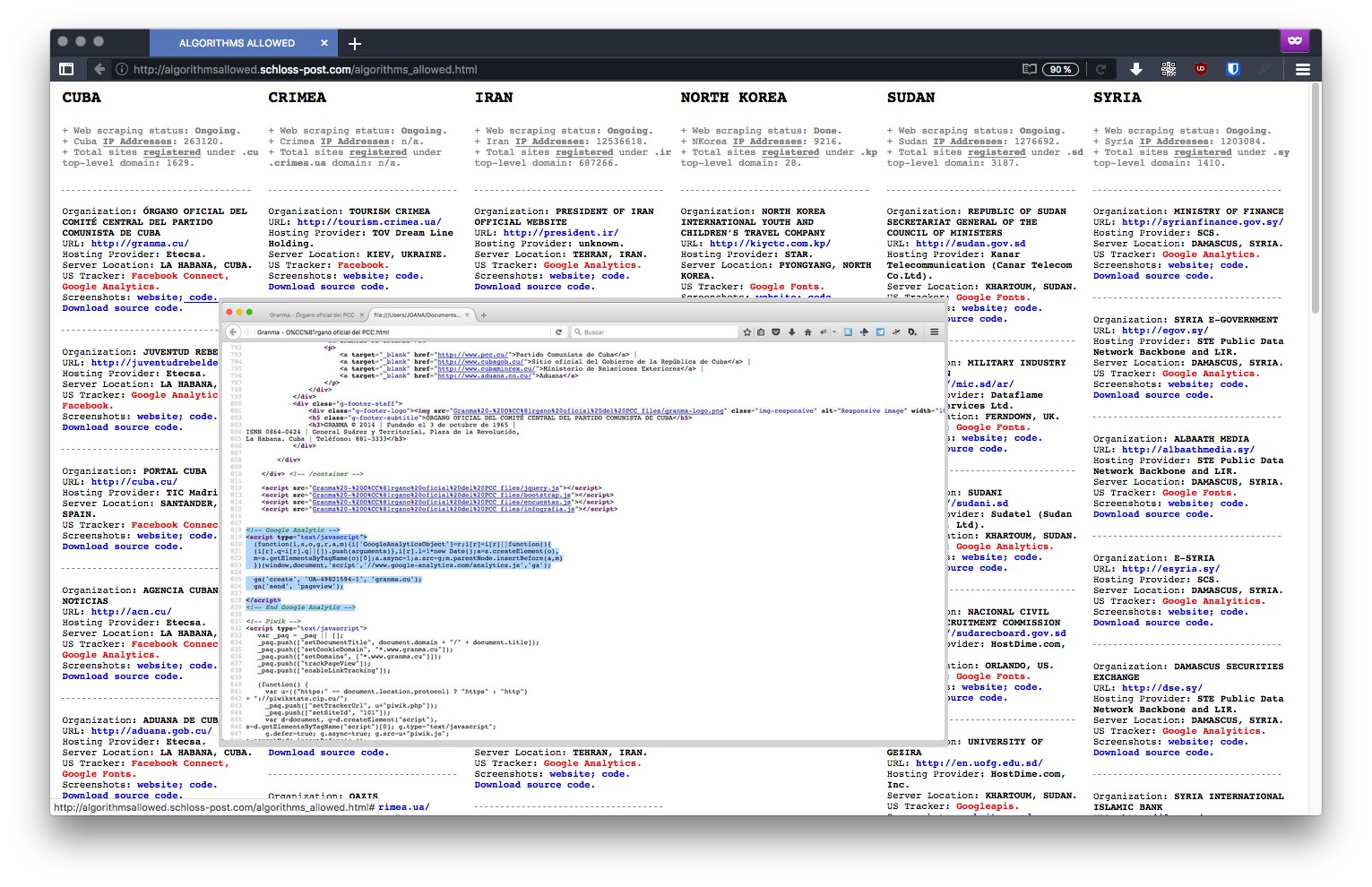
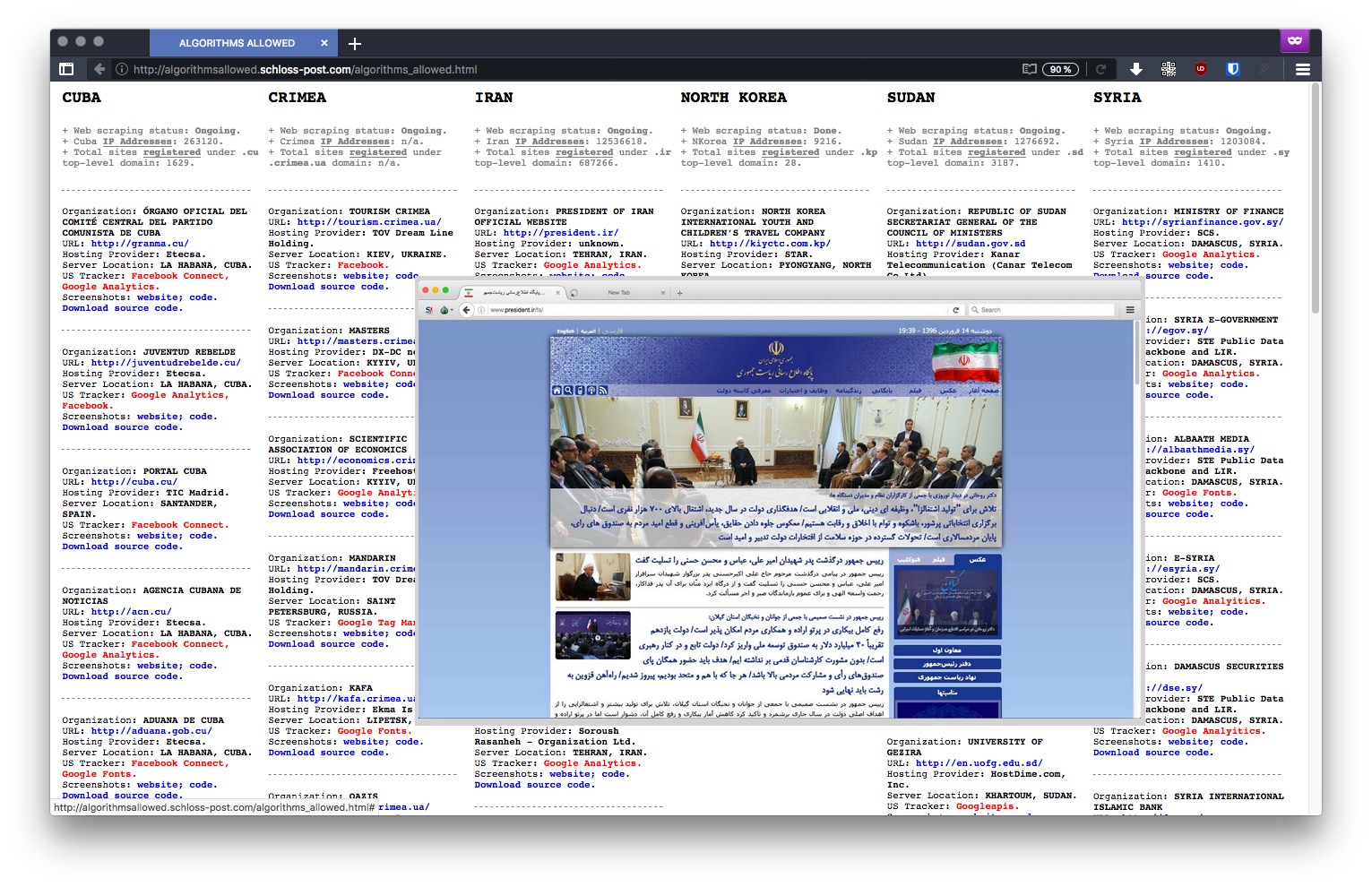
" Typically, a tracker is a piece of code placed within a particular website that allows to monitor and collect data on user behavior. For instance: a tracker can automatically know where a user is based, which computer they’re using, which sites have been visited before accessing a particular site, and which webpages will be accessed in the future – among other more detailed and personal information. The US is currently enforcing embargoes and sanctions against Cuba, Iran, North Korea, Sudan, Syria, and the Ukrainian region of Crimea. "
" This project has been developed as part of the web residency program — Blowing the Whistle, Questioning Evidence - curated by Tatiana Bazichelli for Solitude & ZKM. "
Web résidence du ZKM
J'aime beaucoup ce projet,
la mise en valeur des données, le scraping avec tor
- Crée de la confusion à l'endroit de la propriété des données et de l'information
à l'endroit des États représenté en ligne www - Ils ont en communs d'avoir leur code "occupé" par Google, en "sortant"
- Cela pose des questions de gouvernance #.p
quotes ( homepage project )
" a tracker can automatically know where a user is based, which computer they’re using, which sites have been visited before accessing a particular site "
" American IT giant, have been found within several websites owned by countries under US embargo "
" US is currently enforcing embargoes and sanctions against Cuba, Iran, North Korea, Sudan, Syria, and the Ukrainian region of Crimea "
" It is important to remember that these websites are stored inside hard disks placed in physical territories "
" "ALGORITHMS ALLOWED" unfolds as an ongoing investigation that reveals the many US tracking and online services embedded in websites representing US embargoed countries, thereby exposing the ambiguous relationship between code, public policy, geopolitics, economics, and power in the age of algorithmic governance. "
JavaScript is dangerous! Why? How are websites vulnerable to it? Find out about bug-bounties from @Tom_Scott
Research if the stuff you're including is actually awesome. Only put stuff on the list that you or another contributor can personally recommend. You should rather leave stuff out than include too much.
Ces objectifs peuvent être les suivants :
- collecter des données personnelles (l‘e-mail en tête de liste)
- augmenter le panier moyen
- augmenter le trafic
- favoriser la rétention
- améliorer le taux de clic (sur une publicité par exemple)
WHAT ARE DARK PATTERNS?
Dark Patterns are tricks used in websites and apps that make you do things that you didn't mean to, like buying or signing up for something. The purpose of this site is to spread awareness and to shame companies that use them.
NEW link cette {bulle} :
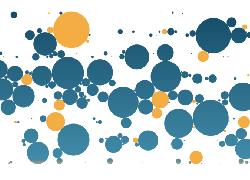
https://informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
OLD
.dead = https://zhenjess.github.io/Breach/
Trends and Patterns
Through the years 2014-2019, there is an upward trend in the number of reported data records breached.
As the amount of data produced around the world increases, the amount of data breach incidents also fluctuates.
Data breachs
-- année après année :
visualisation des failles-fuites de données
XSS tool python check vunerability
HOCXSS is an easy way for the penetration tester and bug bounty hunters to test Cross site scripting. It has featured with crawling, detection parameter discovery, WAF detection capabilities as well.
Leaks of datas
HTTPS , HSTS ,
Referrer Policy ,
Content Security Policy ( CSP )
...
Check security on your website
From : https://neustadt.fr/essays/against-a-user-hostile-web/
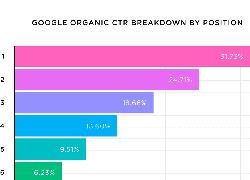
SEO analyse from google
- The 1st Result In Google Gets 31.7% of All Clicks
- Question Titles Have an Above-Average CTR
- Title Tags Between 15 to 40 Characters Have The Best CTR
- Keyword-Rich URLs Are Correlated With a Significantly Higher CTR
...
Upload d'un template basic
--
Ressource templates :
HTML5UP: https://html5up.net/
Introduction à git interactive en français
Comment se déplacer de branche en branches
Multiples commandes, courbe d'apprentissage progressive