↳https://criticalengineering.org/projects/vending-private-network/ ( site )
↳https://julianoliver.com/projects/vending-private-network/ ( JOliver )
à propos de Vending Private Network VPN
In this talk, @Danja_Vasiliev gives an overview of "dark internet topologies" in the context of the commissioned piece //Vending Private Network// he did together with @Julian_Oliver ( 2018 )
Conf
Cite cette carte des câbles sous-marins :
https://www.submarinecablemap.com
Are.na ( adhoc_mesh_ntwrk )
https://www.are.na/vincent-bonnefille/adhoc_mesh_ntwrk
Membre du https://criticalengineering.org
@The_Critical_Engineering_Working_Group
2022 EDIT
- Submarine Cable Map 2015
https://submarine-cable-map-2015.telegeography.com/ - Traceroute mapper ( tool git )
https://stefansundin.github.io/traceroute-mapper/?trace=traceroute%20to%2083.118.202.51%20(83.118.202.51)%2C%2030%20hops%20max%2C%2060%20byte%20packets%0A%201%20%20livebox.home%20(192.168.1.1)%20%204.040%20ms%0A%202%20%2080.10.253.25%20(80.10.253.25)%20%209.688%20ms%0A%203%20%20*%0A%204%20%20*%0A%205%20%20ae51-0.nridf101.rbci.orange.net%20(193.252.98.94)%20%2012.098%20ms%0A%206%20%20*%0A%207%20%20*%0A%208%20%20*%0A%209%20%20*%0A10%20%20*%0A11%20%20*%0A12%20%20*%0A13%20%20*%0A14%20%20*%0A15%20%20*%0A16%20%20*%0A17%20%20*%0A18%20%20*%0A19%20%20*%0A20%20%2051.202.118.83.in-addr.arpa.celeste.fr%20(83.118.202.51)%20%2010.492%20ms%0A - History souces

Via The Critical Engineering Working Group Berlin, October 2011-2019
When Edward Snowden met journalists in his cramped room in Hong Kong's Mira hotel in June, his mission was ambitious. Amid the clutter of laundry, meal trays and his four laptops, he wanted to start a debate about mass surveillance.
He succeeded beyond anything the journalists or Snowden himself ever imagined. His disclosures about the NSA resonated with Americans from day one. But they also exploded round the world.
For some, like Congresswoman Zoe Lofgren, it is a vitally important issue, one of the biggest of our time: nothing less than the defence of democracy in the digital age.
cut :: https://www.theguardian.com/world/interactive/2013/oct/28/nsa-files-decoded-hops
Via Are.na
JavaScript is dangerous! Why? How are websites vulnerable to it? Find out about bug-bounties from @Tom_Scott
" True stories from the dark side of the Internet
This is a podcast about hackers, breaches, shadow government activity, hacktivism, cybercrime, and all the things that dwell on the hidden parts of the network. This is Darknet Diaries. "
-- très bonne série de podcasts sur l'imaginaire hacker, les actualités-retours autours de faits marquant de l'informatique-sécurité contemporaine . Des feuillons, des témoignages... de qualité et accessible (bien qu'en anglais)
Une émission @France_Inter de 2021
https://www.franceinter.fr/emissions/la-chronique-de-thomas-biasci/la-chronique-de-thomas-biasci-du-vendredi-05-novembre-2021
Plusieurs variantes différentes ont vu le jour, les procédures de désinfection sont différentes selon la variante.
Il y a actuellement deux grosses infections discincts :
Une famille qui bloque le PC entièrement (Reveton etc).
Une famille qui bloque simplement le navigateur WEB (Browlock), aucun virus n'est installé sur l'ordinateur, c'est simplement une page WEB qui bloque le navigateur. Il suffit de relancer le navigateur sans réouvrir la page.
R : Salt + hashing for the best !
Hashing Algorithms and Security: http://youtu.be/b4b8ktEV4Bg
Security of Data on Disk: http://youtu.be/4SSSMi4X_mA
Activer le support de GPG dans Claws Mail
NEW link cette {bulle} :
https://informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
OLD
.dead = https://zhenjess.github.io/Breach/
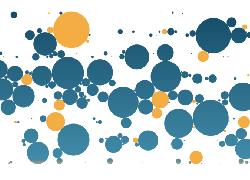
Trends and Patterns
Through the years 2014-2019, there is an upward trend in the number of reported data records breached.
As the amount of data produced around the world increases, the amount of data breach incidents also fluctuates.
Data breachs
-- année après année :
visualisation des failles-fuites de données
XSS tool python check vunerability
HOCXSS is an easy way for the penetration tester and bug bounty hunters to test Cross site scripting. It has featured with crawling, detection parameter discovery, WAF detection capabilities as well.
Leaks of datas
HTTPS , HSTS ,
Referrer Policy ,
Content Security Policy ( CSP )
...
Check security on your website
From : https://neustadt.fr/essays/against-a-user-hostile-web/